 As we’ve discussed both here and on Blue Box, the issue of securing the keys for Secure RTP is one of the remaining challenges to have secure voice transmission in the open standards world of SIP. Out of the large number of proposals to secure the key exchange, “DTLS” emerged as the choice of the IETF… but it still had the issue that an endpoint needed to be sure of the authenticity of the other endpoint’s certificate. SIP Identity (RFC 4474) and a draft “Identity-Media” from Dan Wing addressed the authenticity issue but broke in some common network configurations. Now Kai Fisher has put out an Internet Draft called “End-to-End Security for DTLS-SRTP” that proposes a mechanism to address that. In the post to the SIP mailing list, Kai explains the motivation:
As we’ve discussed both here and on Blue Box, the issue of securing the keys for Secure RTP is one of the remaining challenges to have secure voice transmission in the open standards world of SIP. Out of the large number of proposals to secure the key exchange, “DTLS” emerged as the choice of the IETF… but it still had the issue that an endpoint needed to be sure of the authenticity of the other endpoint’s certificate. SIP Identity (RFC 4474) and a draft “Identity-Media” from Dan Wing addressed the authenticity issue but broke in some common network configurations. Now Kai Fisher has put out an Internet Draft called “End-to-End Security for DTLS-SRTP” that proposes a mechanism to address that. In the post to the SIP mailing list, Kai explains the motivation:
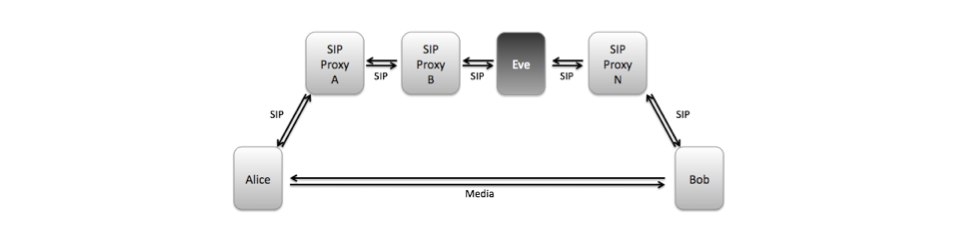
I have submitted a draft proposing a solution to secure a DTLS-SRTP handshake and hence SRTP end-to-end (in terms of end-domain to end-domain). As discussed during the last IETF meetings and analyzed by Dan’s Identity-Media draft, current solutions like SIP Identity do not protect the authenticity of the fingerprint end-to-end in certain inter-domain scenarios. For example, a modification of SDP m-/c-lines or the From header field by intermediaries breaks the SIP-Identity or Identity-Media signature and causes a re-signing by a domain different to the originating one. The draft proposes a solution for such scenarios without the need to re-sign during domain traversal and which preserves the original identity information.
The abstract to the draft provides more info:
The end-to-end security properties of DTLS-SRTP depend on the authenticity of the certificate fingerprint exchanged in the signalling channel. In current approaches the authenticity is protected by SIP-Identity or SIP-Identity-Media. These types of signatures are broken if intermediaries like Session Border Controllers in other domains change specific information of the SIP header or the SIP body. The end-to-end security property between the originating and terminating domain is lost if these intermediaries re-sign the SIP message and create a new identity signature using their own domain credentials.
This document defines a new signature type ‘Fingerprint-Identity’ which is exchanged in the signalling channel. Fingerprint-Identity covers only those elements of a SIP message necessary to authenticate the certificate fingerprint and to secure media end-to-end. It is independent from SIP-Identity and SIP-Identity-Media and can be applied in parallel to them.
More details can, of course, be found in the draft. As noted in the post to the SIP mailing list, Kai is looking for feedback. This is an important issue to get done – and to get done correctly – so we strongly urge people to take a look at the document and provide feedback if you see ways the proposal can be improved.
Technorati Tags:
SIP, SRTP, IETF, standards, sip security, voip security, security, DTLS
 Blue Box
Blue Box 