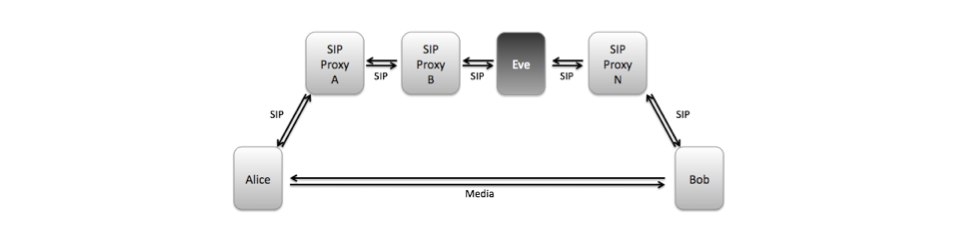
At a recent conference where I spoke about VoIP security, a researcher at a government agency (and if I recall correctly, also a part-time professor at a university) approached me afterward and asked if I knew of any “audit methodology” for analyzing VoIP systems, especially from a forensic point-of-view. I did not… but thought I’d ask the question here?
Is anyone aware of any work to define a methodology for auditing VoIP systems?
(If not, it sounds like a great project for a group like VOIPSA to take on. Anyone interested in heading up such a working group?)